HIPAA encryption requirements keep Protected Health Information (PHI) properly safeguarded from cybercriminals and data breaches. The Health Insurance Portability and Accountability Act (HIPAA) outlines these requirements. They apply to Covered Entities (CE) that regularly handle PHI.

For Example, a CE can include any of the following.
- Physicians
- Physician’s Assistants
- Pharmacists
- Nurses
- Medical Billing Personnel
- Insurance Providers
- Therapists
- Dentists
- Psychologists
- Nursing Homes
Healthcare organizations must comply with HIPAA encryption requirements. Data security is a vital aspect of the medical industry because of the sensitive information they handle.
It is crucial that these organizations and the medical personnel on their staff comply with HIPAA regulations. This way, they can not only keep their patient’s private medical information protected, but also avoid a dangerous data breach. Keep reading to learn more about how HIPAA laws and encryption safeguard PHI!
HIPAA Rules & Safeguards
HIPPA laws are in place to protect a patient’s PHI. There are three general rules outlined under HIPAA – The Privacy Rule, The Security Rule, & The Breach Notification Rule. Each one serves a unique purpose in regard to safeguarding PHI.

The Privacy Rule protects the confidentiality & integrity of a patient’s private medical information. It regulates who can access PHI and under what circumstances it can be disclosed.
The Breach Notification Rule states that a CE and their BAs must tell people if there is a data breach. This rule only applies if there has been a compromise of improperly secured health information.
The Security Rule specifically focuses on safeguarding Electronic Protected Health Information (ePHI). It establishes security standards HIPAA covered entities must implement & maintain to keep electronic health records secure.
In regard to encryption requirements for data in transit, The HIPAA Security Rule will be most notable. There are three specific security measures outlined under The Security Rule: Technical, Physical, and Administrative Safeguards.
You can find HIPAA encryption requirements under The Security Rule’s Technical Safeguards. They are specific to protecting ePHI. However, these requirements are “addressable” under HIPAA law. CEs can use an alternative method to safeguard their data if it is as effective as encryption.

Additionally, the CE must also provide proper justifications for using the alternative method. In many cases, however, when properly safeguarding ePHI, encryption often proves to be the most effective method.
HIPAA Encryption Requirements for Data in Transit
HIPAA encryption requirements make ePHI completely anonymous to individuals who may want to gain unauthorized access to it. An encrypted message is the most effective way to send ePHI securely. Therefore, it is crucial that healthcare organizations implement these guidelines when handling confidential data.
You can apply encryption to data at rest and data in transit. Data at rest is not in motion. It is typically stored on a laptop, USB drive, or computer system.

You may not always need to encrypt data at rest, especially if you only send and store the ePHI internally. Encryption requirements for data in transit, however, can be much different.
What is Data in Transit?
Data in transit is in motion. This means it is traveling from one device to another. For example, physicians may share ePHI via email, chat service, or upload medical records to a cloud storage system.

This data passes through multiple servers while it is transit. Therefore, it is extremely susceptible to unauthorized access. If it falls into the wrong hands, the responsible party could face severe fines and penalties for non-HIPAA compliance.
Why Do HIPAA Encryption Requirements Exist?
HIPAA encryption requirements make ePHI completely unreadable while it is in motion. The only way to access it again is with a secure decryption key. In fact, experts estimate that encryption code properly safeguards ePHI for over 1.5 million years!
Data encryption is a complex algorithm that strips ePHI of all identifiable factors. It makes this confidential information look like nonsense as it travels across the internet.
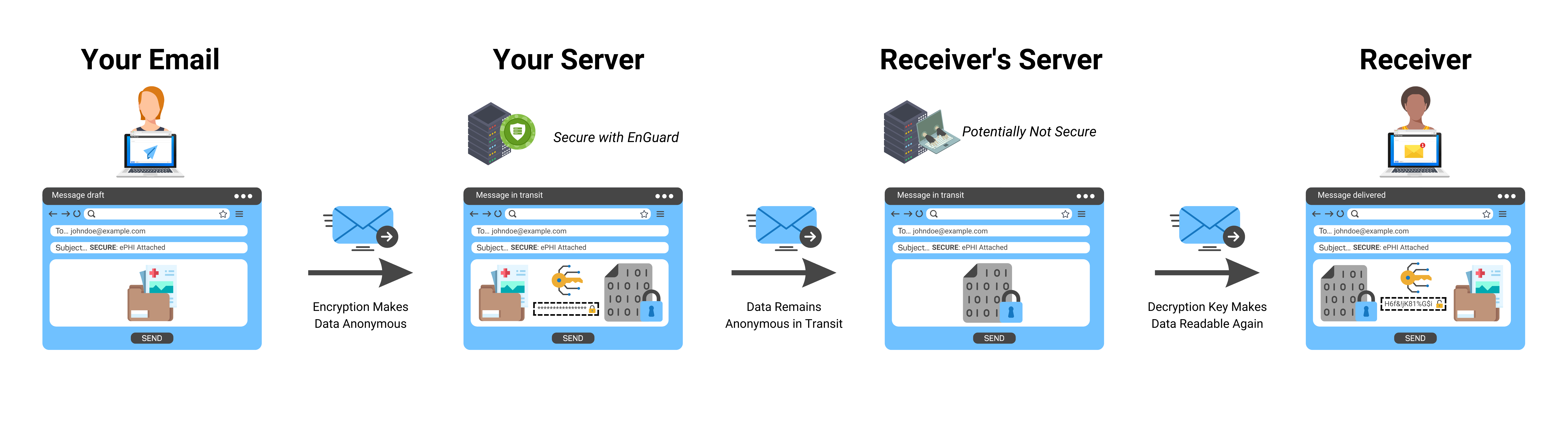
HIPAA encryption requirements go farther than solely protecting data at rest. It keeps ePHI anonymous while in travels from server to server. In addition, the data stored on the servers also remain encrypted. Even if unauthorized personnel attempt to access it- the anonymous, encrypted data is utterly useless unless they have the private key.
As a healthcare provider, avoiding hefty fines for non-HIPAA compliance is vitally important for your organization’s reputation. More importantly, you have an ethical responsibility to uphold the integrity of your patient’s medical information. HIPAA encryption requirements exist to protect healthcare organizations and the ePHI they handle. That being said, following HIPAA encryption requirements is the most effective way to avoid the detrimental impacts of a data breach.
ePHI…
ePHI stands for electronic Protected Health Information. HIPAA encryption requirements are in place to keep ePHI properly safeguarded from unauthorized access.
The ePHI must contain individually identifiable factors to be protected under HIPAA. These are a broad range of characteristics that make health data traceable to a specific patient.
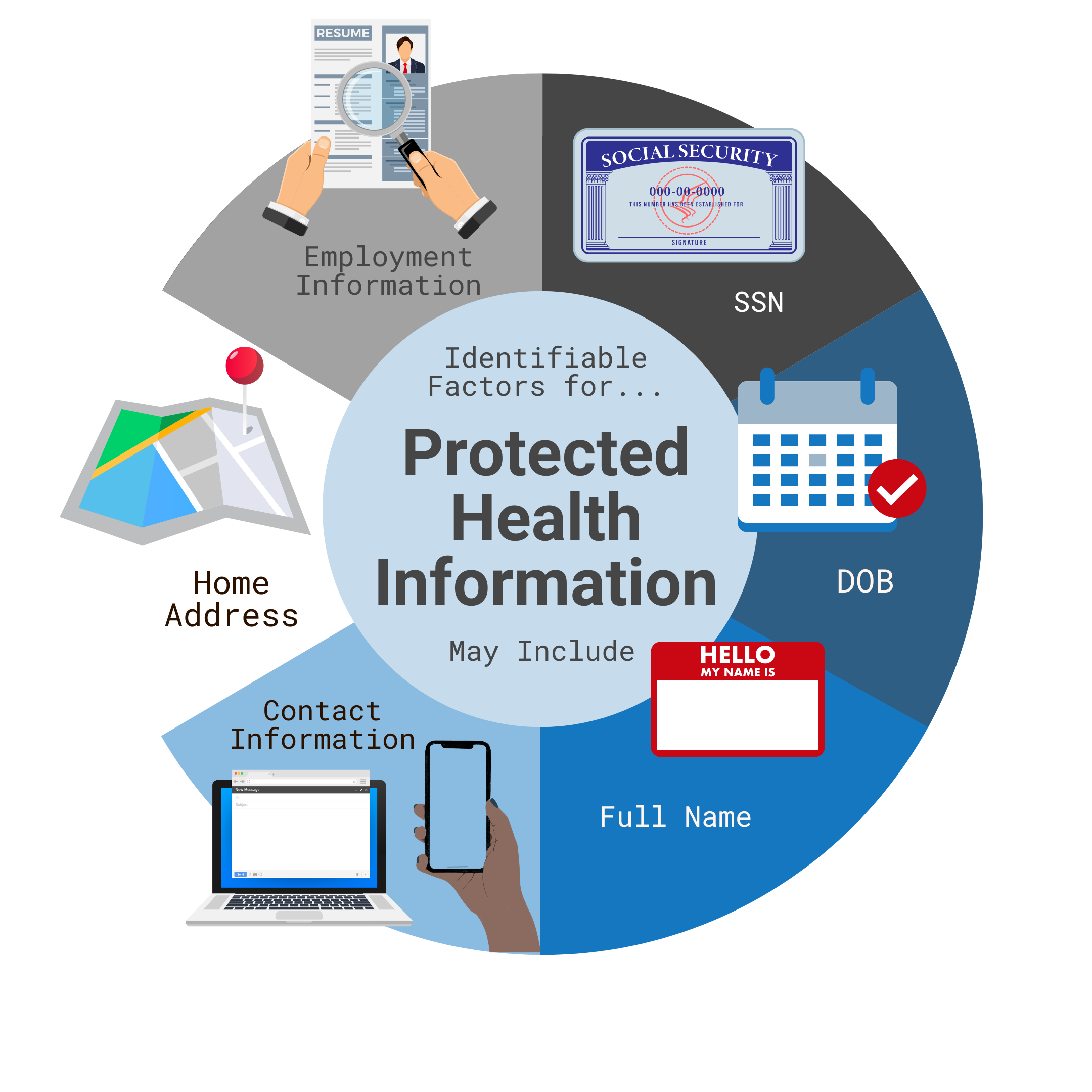
What are the Most Common Reasons for Data Breaches
Weak or Stolen Passwords make the devices you use to store ePHI extremely vulnerable. In fact, there are nearly 1,000 password-based hacking attack attempts made every second. While a simple password may be easy to remember, it can make your organization susceptible to a data breach. Use a strong password with a variation of numbers, letters, and symbols to keep ePHI as secure as possible!
Phishing Emails trick users by posing as trustworthy organizations to steal personal information. Once hackers obtain personal details, they use them to commit serious cybercrimes. There are over 3 billion phishing emails sent every day, making them an extremely common cause for a data breach. Beware of urgent emails with strange links, unknown addresses, or spelling mistakes, as they could be trying to hack you!

Human Error is still a driving force behind many data breaches. Even in a culture immersed in digital technology, human errors still account for over 80% of data breaches. Employees may be tricked by phishing, neglect risk assessment, or mishandle sensitive files. You can help avoid this by training employees about proper procedure and hacking attempts to minimize your risk of a data breach.
HIPAA Encryption Requirements Safeguard ePHI!
At Enterprise Guardian®, meeting HIPAA encryption requirements have never been easier! As a valuable EnGuard® client, you can rest assured that any confidential information you send will remain anonymous through email encryption.
It is important to remember that not all email services are secure. Through encryption technologies, our team can provide you with an email address that is safe and HIPAA compliant!

For as little as $10 per month, our security solutions help Healthcare entities uphold the security standards that HIPAA requires. Secure email is just a few clicks away! For information about our services, look at our pricing page today.

